
Today, it is possible to intercept communications by means of a number of electronic devices that can be no larger than a box of matches and easily concealable in a number of places. The most classic device is the covert transmitter.
ELECTRONIC COUNTERSURVEILLANCE
SURVEILLANCE METHODS AND DEVICES
 |
Today, it is possible to intercept communications by means of a number of electronic devices that can be no larger than a box of matches and easily concealable in a number of places. The most classic device is the covert transmitter. |
| This piece of equipment
transmits to a listening post (where appropriate recording devices will be
installed) all sounds (in particular conversations) generated in one or
more rooms.
|
| Telephone transmitters instead intercept conversations (or fax-data transmissions) through telephone lines and frequently drain their operational power directly from the line. Due to absence of a battery (that needs to be periodically substituted), these types of transmitter are particularly dangerous as their "operational life" is practically unlimited. |  |
 |
When audio interception is not sufficient, covert video-cameras can be used to transmit live video via radio or wire. |
|
Even a common tape-recorder can become a good interception system. Electrical or electronic cables that pass in a room can be used in order to connect a hidden microphone and modem equipped computers can transmit worldwide audio or video signals or can be "infected" with surveillance software or hardware systems. A room's windows can be "illuminated" from the outside by an Infrared or LASER beam that is "modulated" by the window's micro-vibrations caused by voice's sound energy. Even a common air-conditioning duct or water pipe that passes through a room can become a surveillance tool in the hands of an intruder.
|
 |
Covert radio transmitters usually use traditional modulation (AM or FM) systems, however particularly advanced transmitters will use advanced digital systems (Infinity, Frequency Hopping, Burst, Agile, Spread Spectrum). In this case, only the use of dedicated instruments (Digital Spectrum Analyzers and Non Linear Junction Detectors) by specialized technicians will reveal their presence as more common frequency counters or broadband receivers will not be sufficient. |
| Running specialized software on a Computer controlled Digital Spectrum Analyzer gives us the possibility to document and memorize the radio spectrum conditions of the area to be swept. |
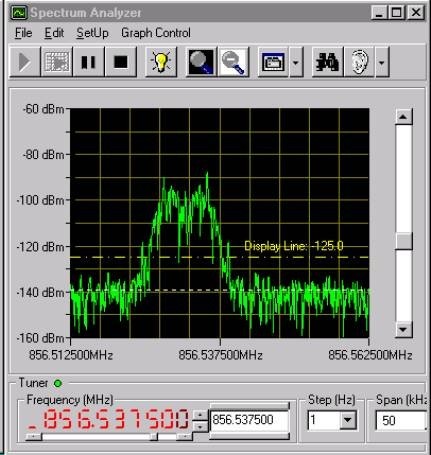 |
 |
Switched-off or no longer functioning surveillance devices can only be indicated by use of a Non Linear Junction Detector. This expensive instrument is not commonly found in Europe and for maximum effectiveness must be used by properly trained investigative technicians. |
| Bug sweeping of telephone, electrical and data lines, in particular when the analysed cable is of a length of hundreds if not thousands of metres, can only be conducted by means of a particular instrument called Time Domain Reflectometer (TDR). This piece of equipment can check any type of line (even under power) and indicates on a display screen the presence of abnormalities (short circuits, open circuits, series or parallel connections, inductances, capacities, etc.) and/or parasites. |
|
| Our
digital Time Domain Reflectometer has a range of over 11.000 metres with a
localization precision of about 20/30 centimetres. This instrument is
indispensable when the examined line is very long (try to imagine the
route that a cable follows from a telephone switchboard in the basement of
a large building to a phone located at the top floor) and not easily
accessible (passing through walls, third party property, roads, etc.).
|
|
|
WARNING SIGNS
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
| If you recently have noticed one or more of these warning signs, you may be the object of covert surveillance. If you decide to contact us for a consultation or counter-surveillance sweep talk about your decision only with who must know and call us from a secure phone that is not situated in the suspect offices or home.
|
HOW A COUNTER-SURVEILLANCE SWEEP IS CONDUCTED
 |
Upon arrival at the sweep site with our mobile counter-surveillance laboratory (designed for Europe-wide travel), our Investigative Technicians will conduct a number of inspections that for logistic and security reasons are preferably carried out during weekends or after normal office hours: |
|

|
 |
|
||
|
|
 |
||
|
|||
|
|
||
|
|
||
|
|
At the end of our inspection, we shall deliver a detailed technical report together with a list of suggestions and solutions for site security optimization.
|